How I hacked my friends website...
Just this morning my friend contacted me requesting that I check his web application for bugs. His app was tied to a business card he made. My friend was careful, just not careful enough :)

Max vonBlankenburg – 2/6/2021
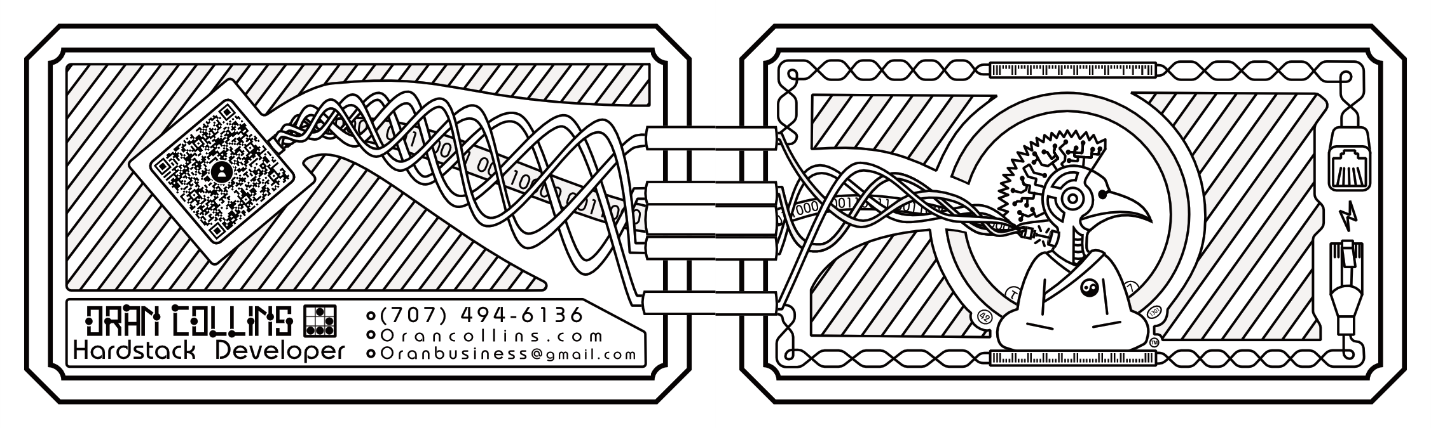
Just this morning my friend contacted me requesting that I check his web application for bugs. His app was tied to a business card he made (fig. 1) that had an ARG-type challenge on it. There were three numbers that could be derived from the card, and the purpose of the app was to check those three numbers to see if they were the correct puzzle numbers.
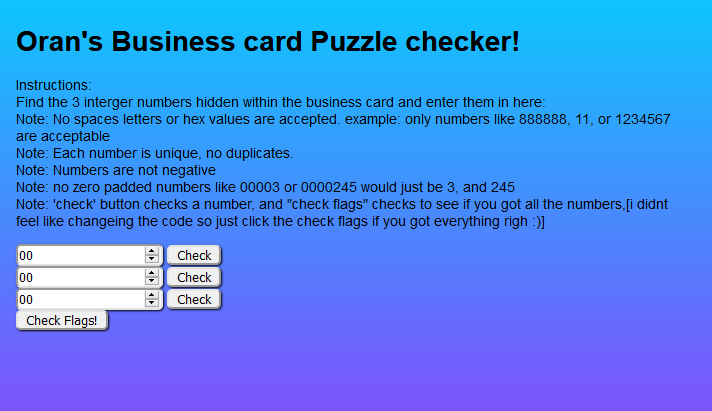
The app had three submission forms (fig. 2), and the user could either check one number at a time or all three. Each submission made a GET request to a subdomain of http://orancollins.com:3333and checked the numbers on the server side. There were no client-side cookies or source files that gave away the answers through a simple view source.
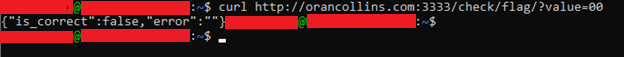
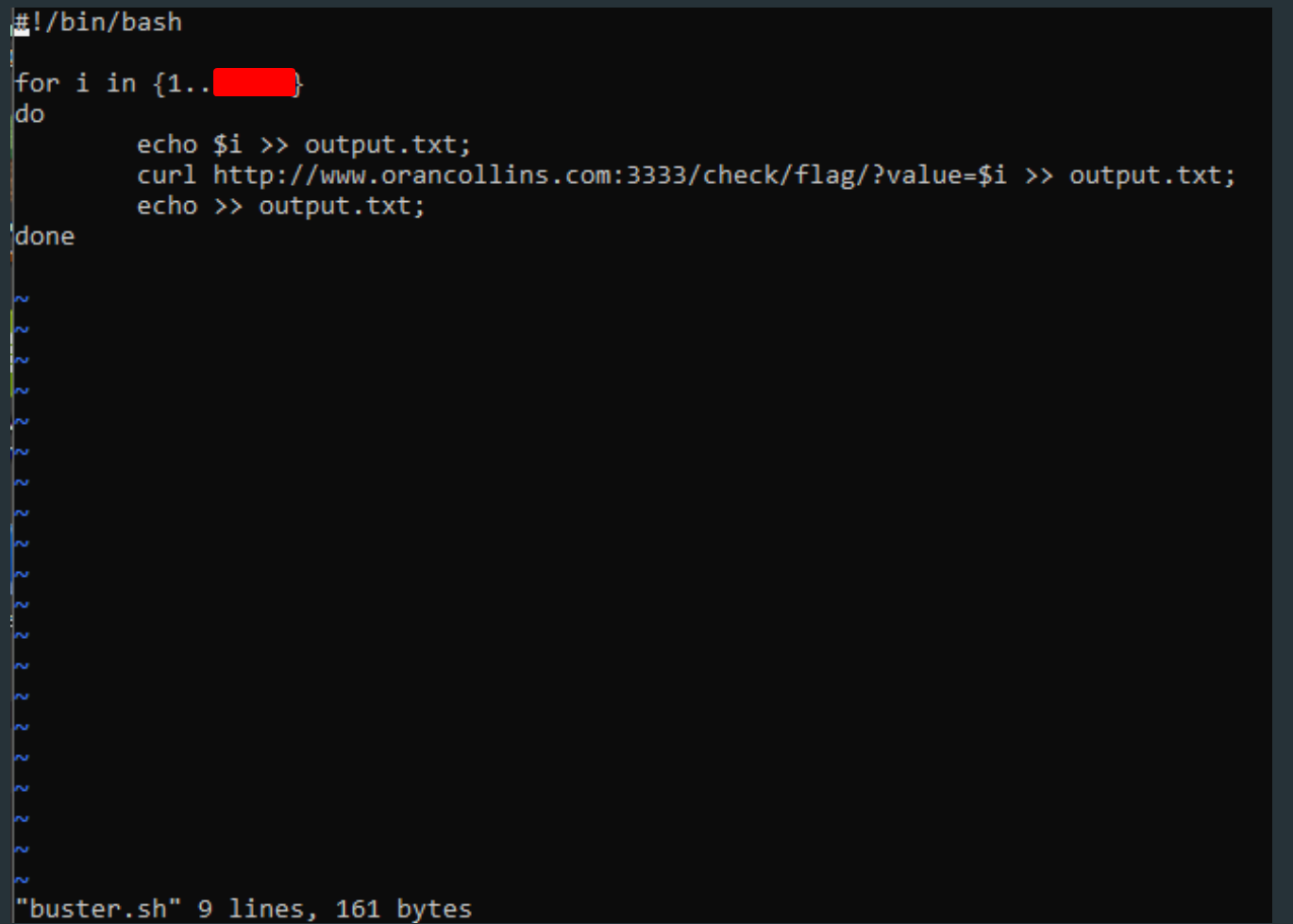
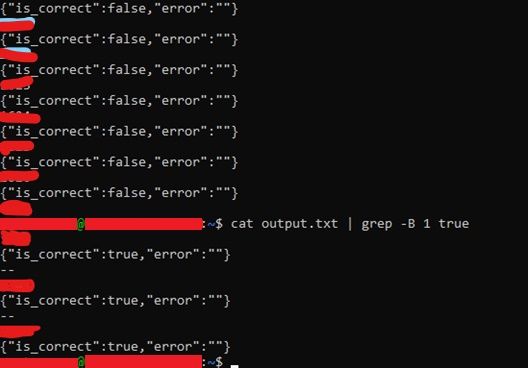
To test the server’s resistance to brute-forcing, I first tried to make a GET request to http://orancollins.com/check/flag/?value=00. I got a JSON object in response (fig. 4) that revealed that “0” was not the correct number. I then proceeded to write a shell script to enumerate over positive integers starting from 1 (fig. 5). The shell script ran for about half an hour (?), with intermittent timeouts (reason unknown), and by about the  'th enumeration I obtained three “true” responses. I then entered the numbers corresponding to the responses into the web application and they successfully validated.
'th enumeration I obtained three “true” responses. I then entered the numbers corresponding to the responses into the web application and they successfully validated.

Created by
by Max vonBlankenburg
github.com/APstarwars
Date:
2/6/2021

